Sentinel can integrate with customer SIEM platforms for hybrid cloud monitoring use cases, using specialized threat detection algorithms and sending high fidelity alerts to these platforms.
While there may be a few different architectures to achieve this integration, surely Azure Event Hub can provide an enterprise grade system for alert streaming. Event Hub is designed for very high scale event and message streaming using a number of event producers and consumer groups.
In our case, and from a security perspective, it will provide a single platform to buffer and stream alerts from different sources (i.e Azure Sentinel, Azure Security Center, Microsoft Defender ATP) and ideal for scenarios where customers use Kafka technologies to collect events
Being Event Hub a key component of this architecture, it’s worth noticing the following concepts:
- Azure Event Hub uses ‘consumer groups’ which read from the platform on ‘pull mode’
- We will recommend the use of Event Hub Standard and not Basic. The Standard tier of Azure Event Hubs provides features beyond what is available in the Basic tier. Also, Event Hubs Standard tier currently supports a maximum retention period of seven days. Event hubs are not intended as a permanent data store. Retention periods greater than 24 hours are intended for scenarios in which it is convenient to replay an event stream into the same systems;
- The following features are included with Standard:
- Longer event retention
- Additional brokered connections, with an overage charge for more than the number included
- More than a single consumer group
- Capture (i.e to send events to a blob container)
- Kafka integration
Assuming you already have an Azure tenant, a subscription and Azure Sentinel onboarded on a Log Analytics workspace, a QRadar instance with the Azure Event Hub protocol and DSM, then as a minium, in order to integrate both platforms you will need to follow these steps:
- Enable Microsoft Graph Security API in your tenant
- Event Hub namespace, with one Event Hub entity and one consumer group (not on $default).
- Expose Event Hub and blob storage connnection strings to QRadar
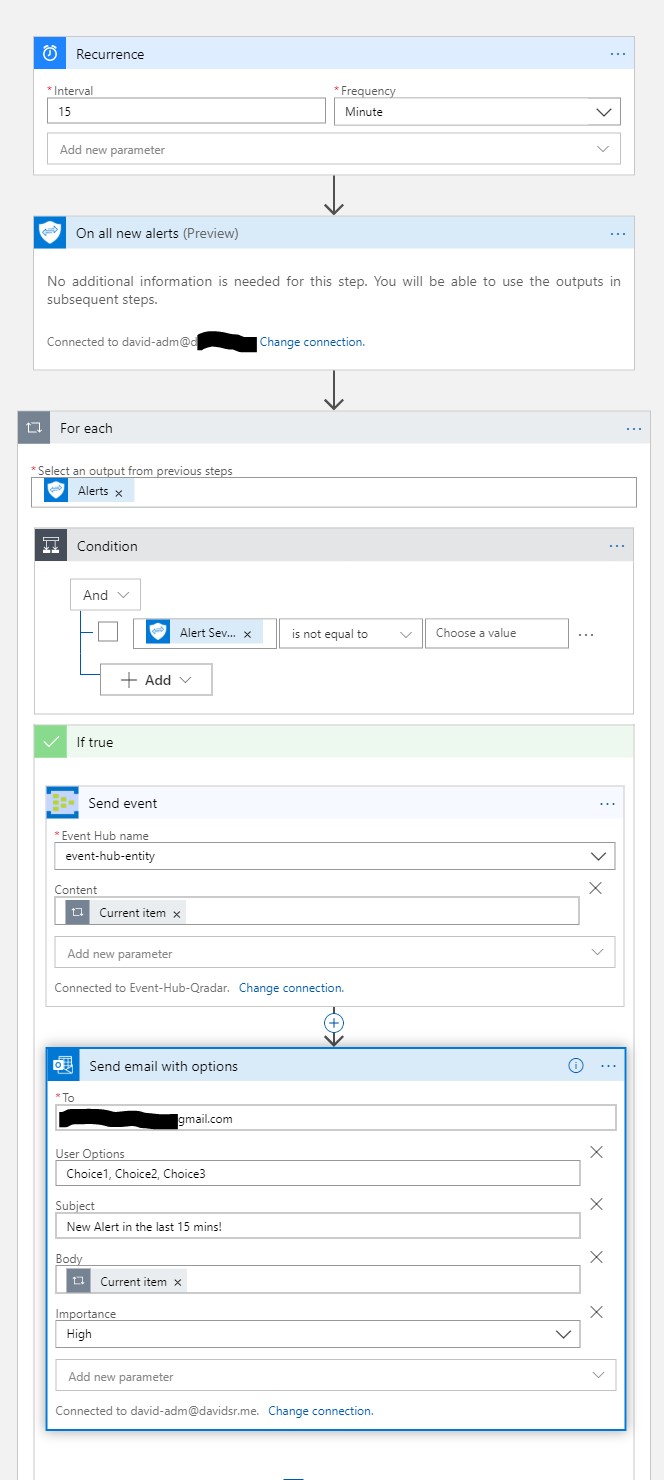
- Logic App or Sentinel playbook:
- Schedule to read new alerts from Graph Security API every X mins
- Send events to the Event Hub consumer group
The following events on QRadar will show alerts detected by an Analytics query scheduled in Sentinel. That’s why you will see “provider”: “azure sentinel”
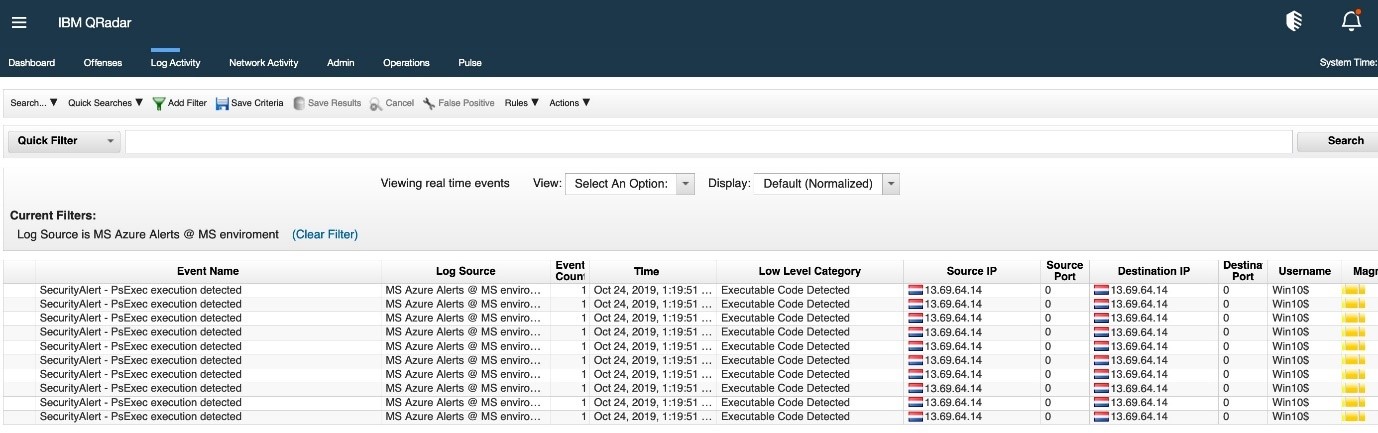
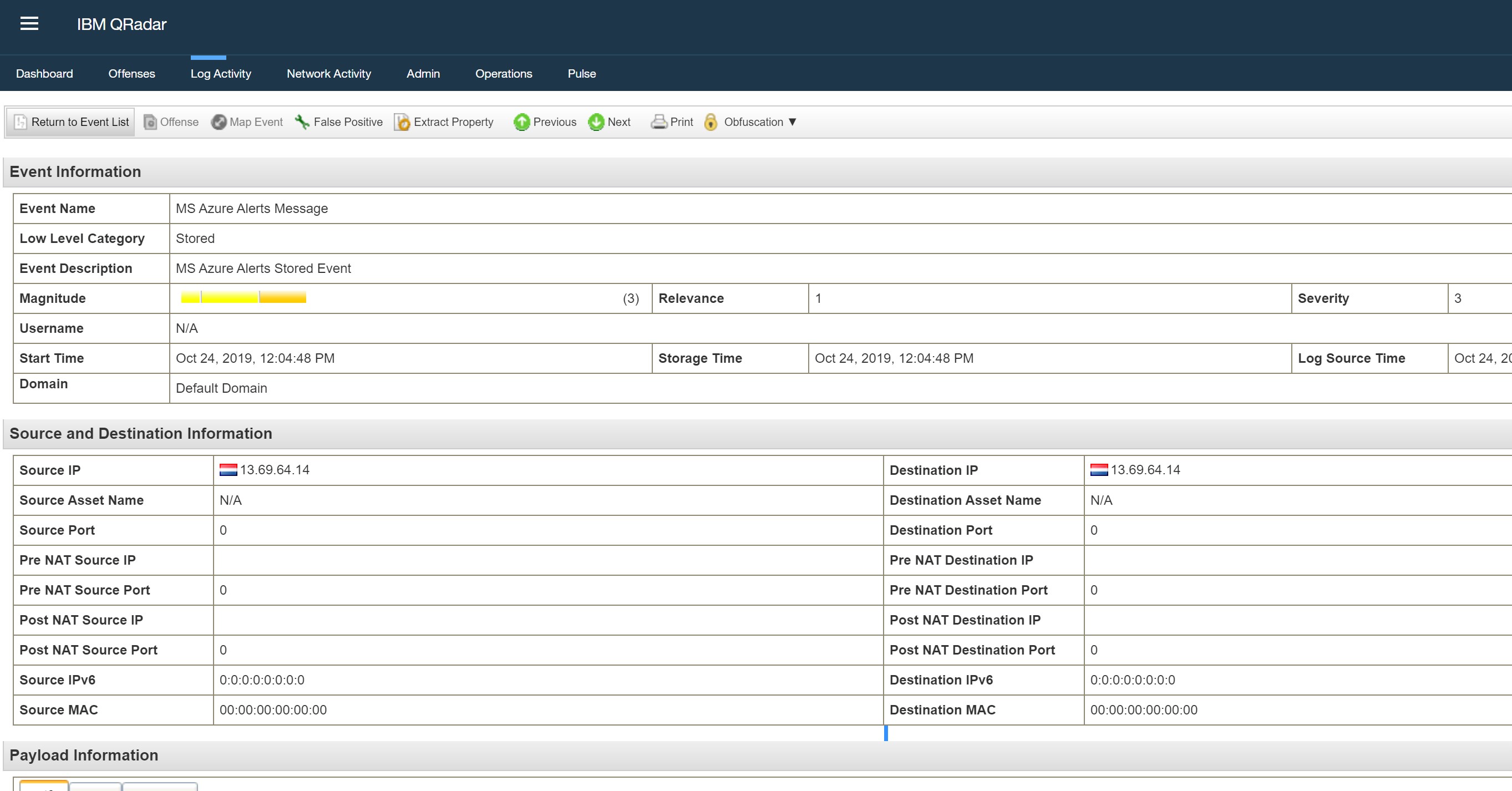
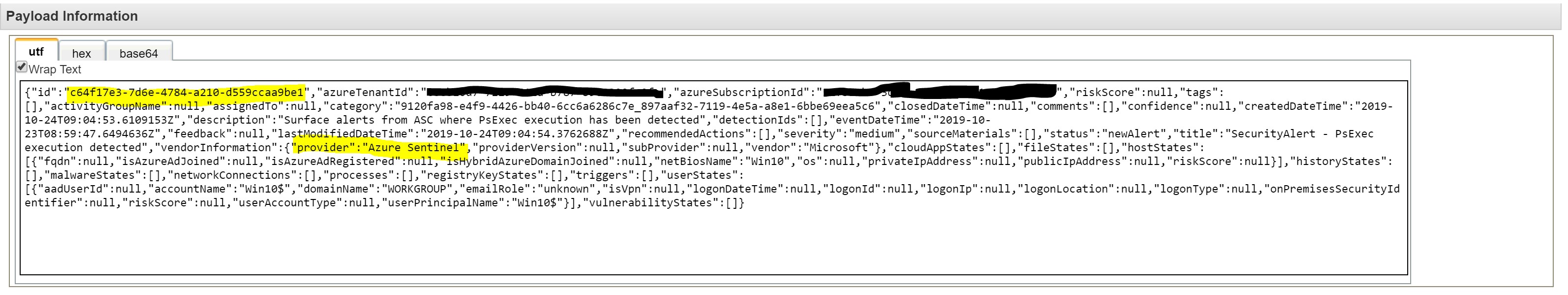
You may also see events detected by ASC (Azure Security Center) when you have enabled the connector to Sentinel

We can search the “AlertID” in Sentinel
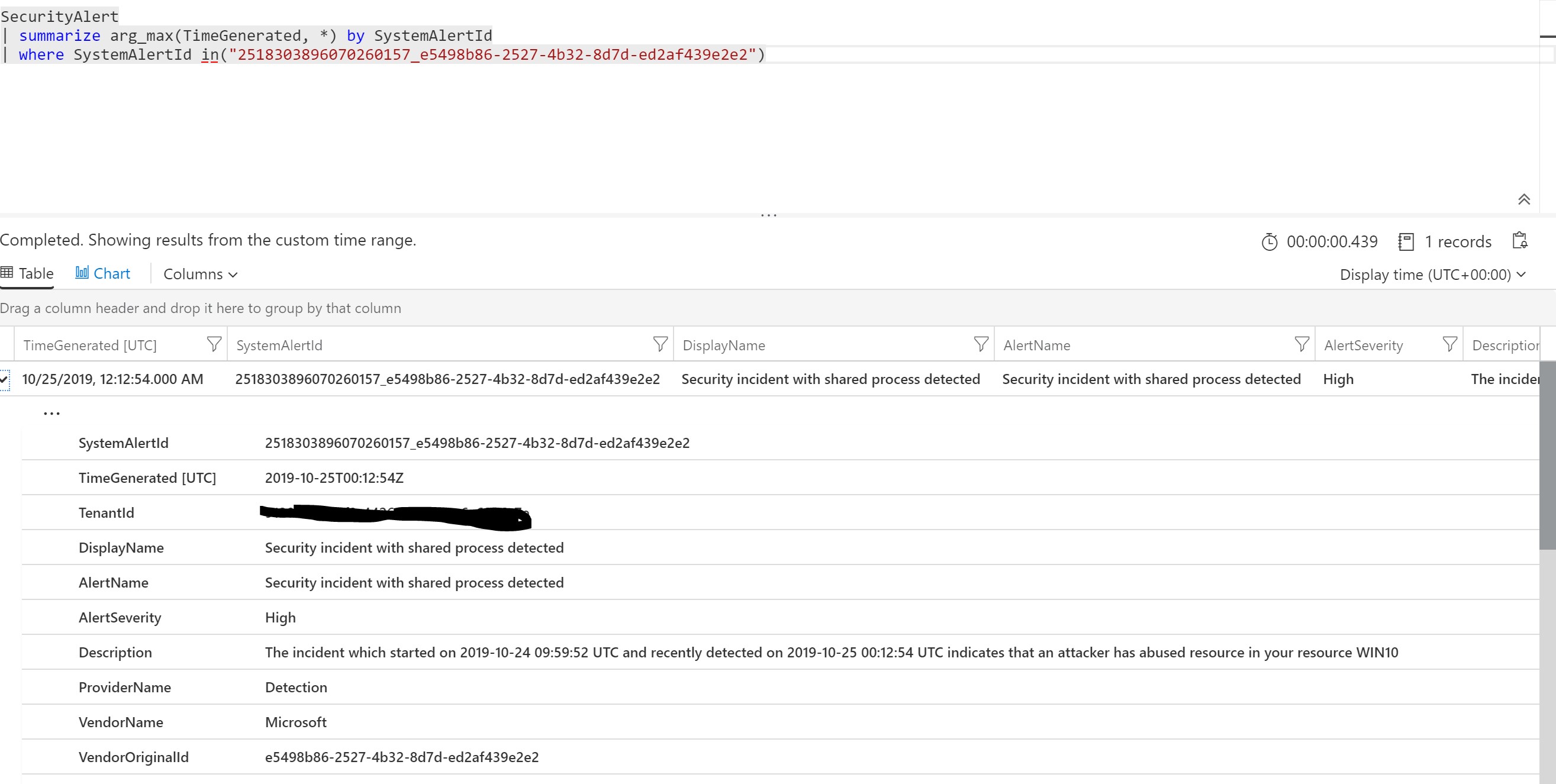
Azure LogicApp reading new alerts from the Graph Security API
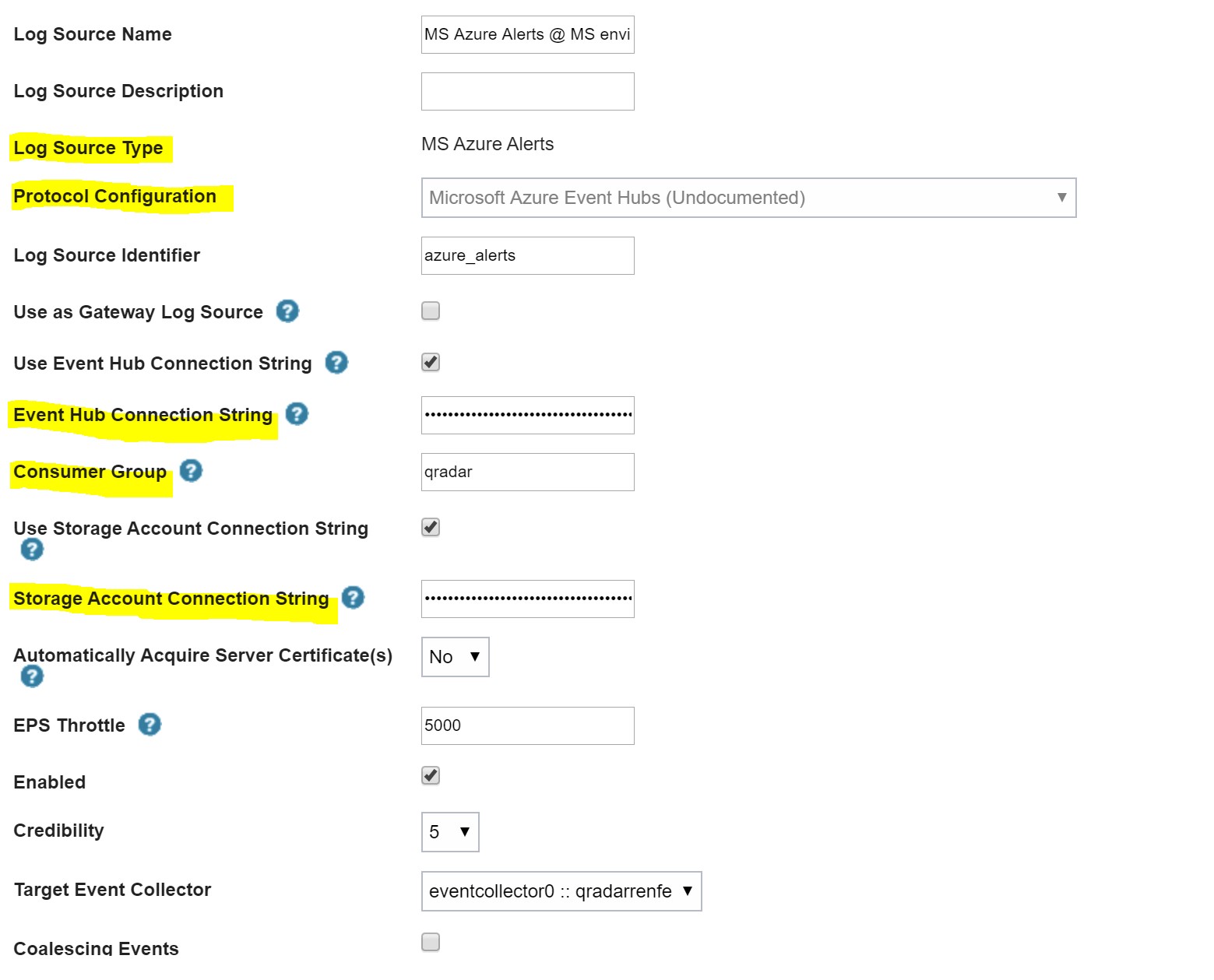
On QRadar, we have added a Log Source for Azure Event Hub. This needs access to your Event Hub through a connection string and a storage account connection string
0 Comments