On this post I will run through the necessary steps to integrate Azure Sentinel with Palo Alto VM-Series Firewall logs. First things first, we will assume you already have an Azure Sentinel workspace created. We will go ahead, open our Sentinel portal in Azure and on the ‘Connectors’ blade click on the Palo Alto connector
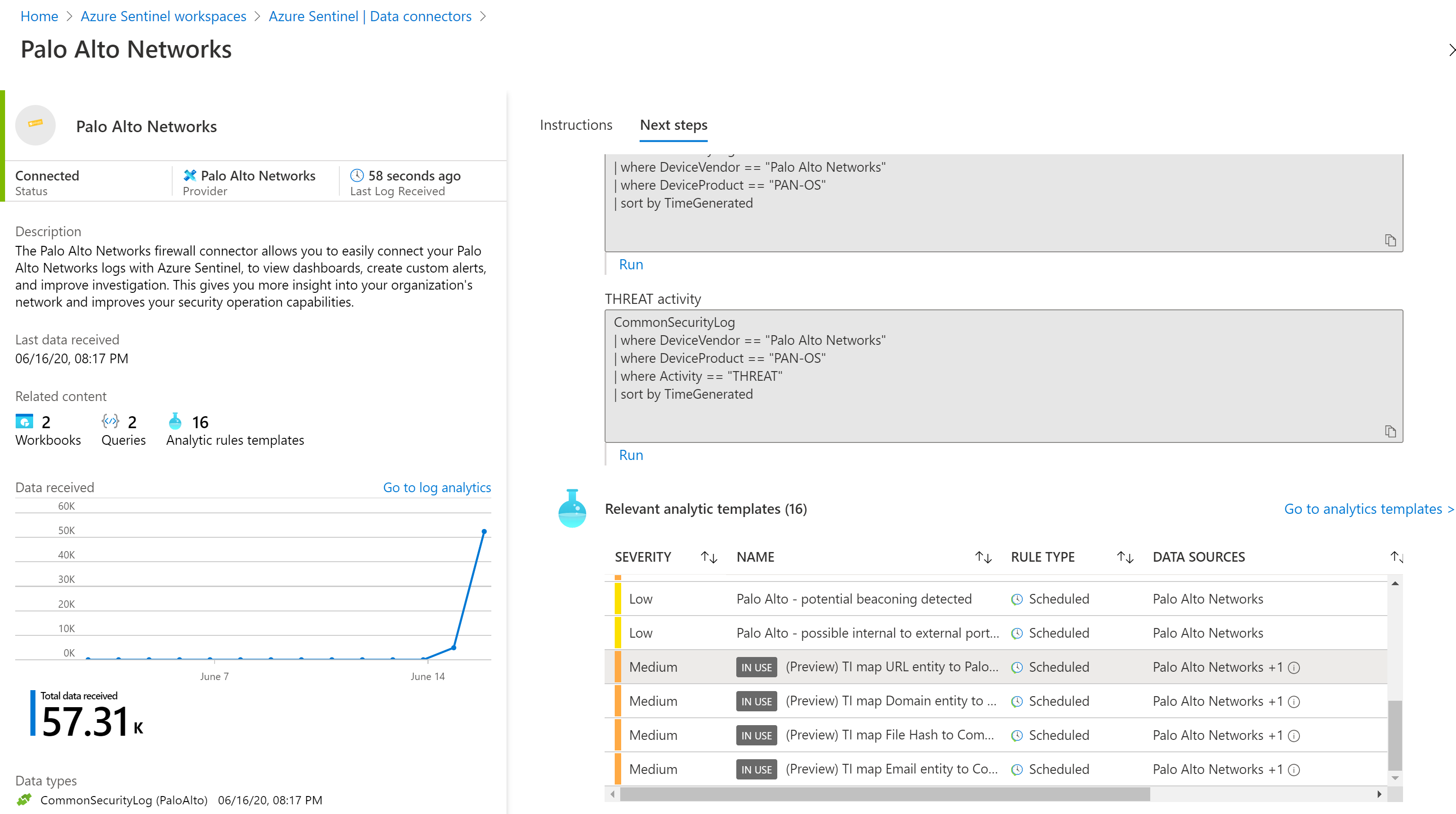
The Palo Alto Networks firewall connector allows you to easily connect your Palo Alto Networks logs with Azure Sentinel, to view dashboards, create custom alerts, and improve investigation. This gives you more insight into your organization’s network and improves your security operation capabilities.
We will also assume you already have a Linux machine that Azure Sentinel will use as the proxy between your Palo Alto firewall and Azure Sentinel to collect the relevant logs. This machine can be on your on-prem environment, Azure or other clouds
As documented on the Sentinel configuration for Palo Alto, you will also install the Microsoft Monitoring Agent on your Linux machine and configure the machine to listen on the necessary port and forward messages to your Azure Sentinel workspace. The Syslog/CEF collector collects CEF messages on port 514 TCP
On the Palo Alto side, we need to forward Syslog messages in CEF format to your Azure Sentinel workspace (through the linux collector) via the Syslog agent.
Go to Palo Alto CEF Configuration and Palo Alto Configure Syslog Monitoring steps 2, 3, choose your version, and follow the instructions using the following guidelines:
I have documented those steps here. On your Palo Alto console, you will need to configure a Syslog server that points to your log collector, in my case a virtual machine running on Azure. Make sure you use the format ‘BSD’ and transport protocol is ‘TCP’. You need to edit the custom log format as explained here https://docs.paloaltonetworks.com/resources/cef
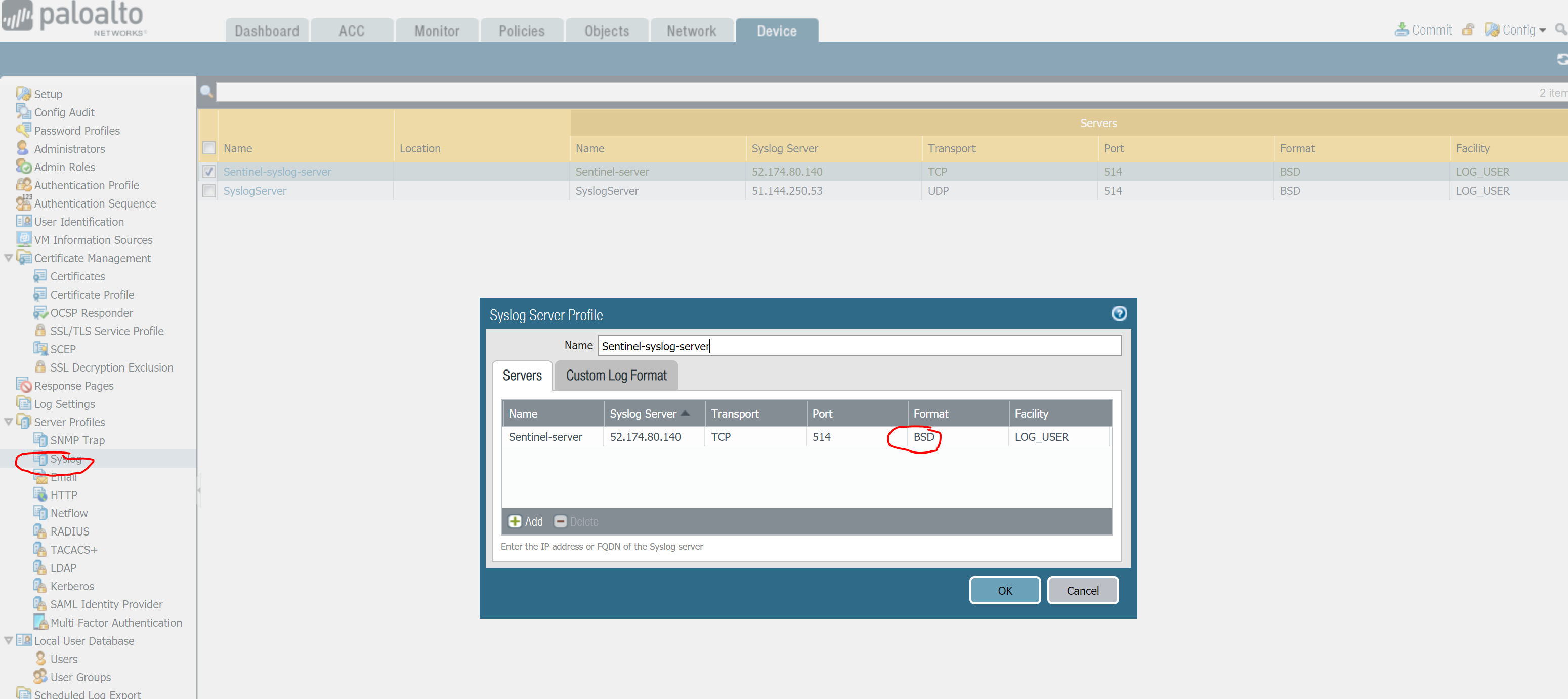
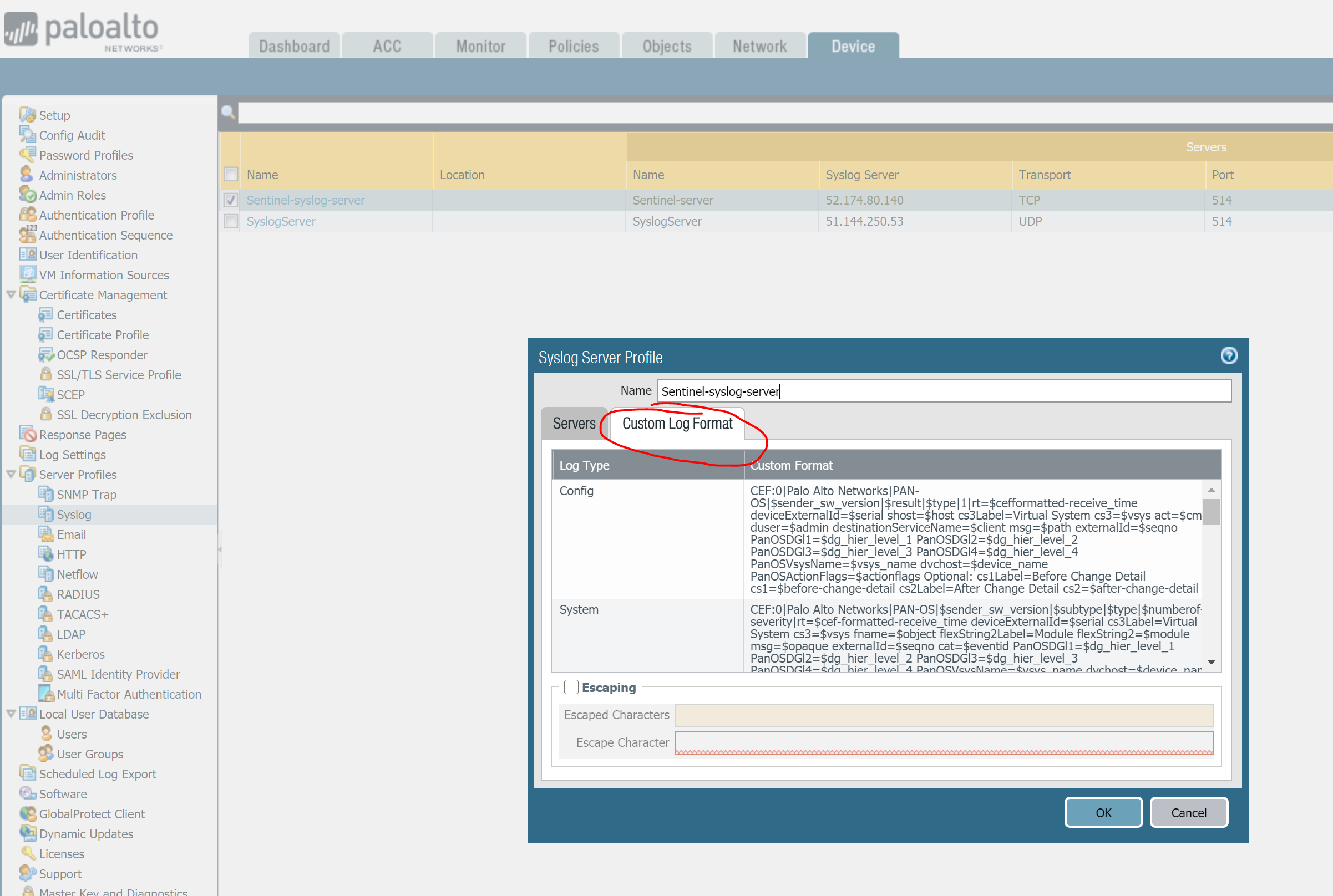
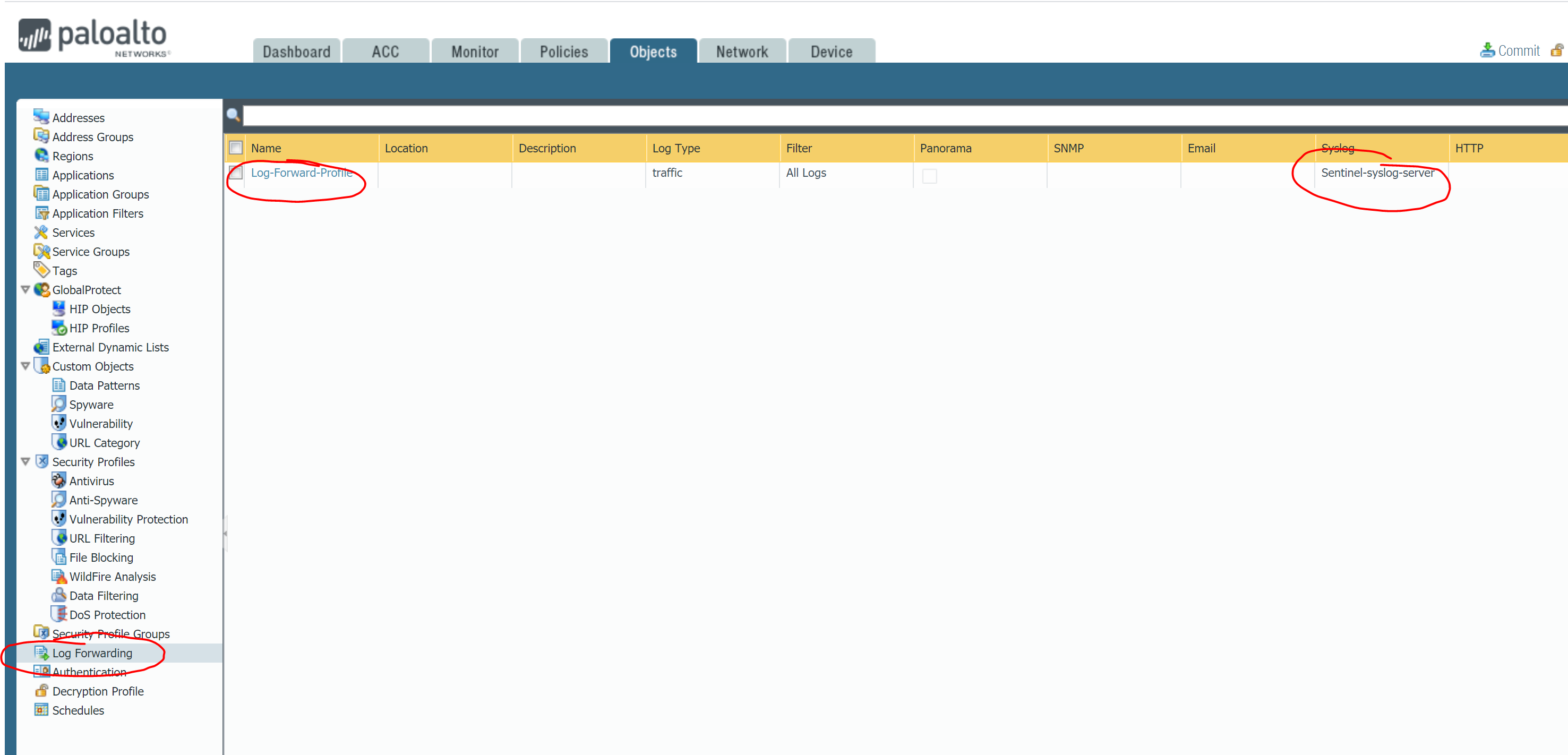
Once you are done with the syslog server your next step is to configure Log Forwarding using the server profile just created
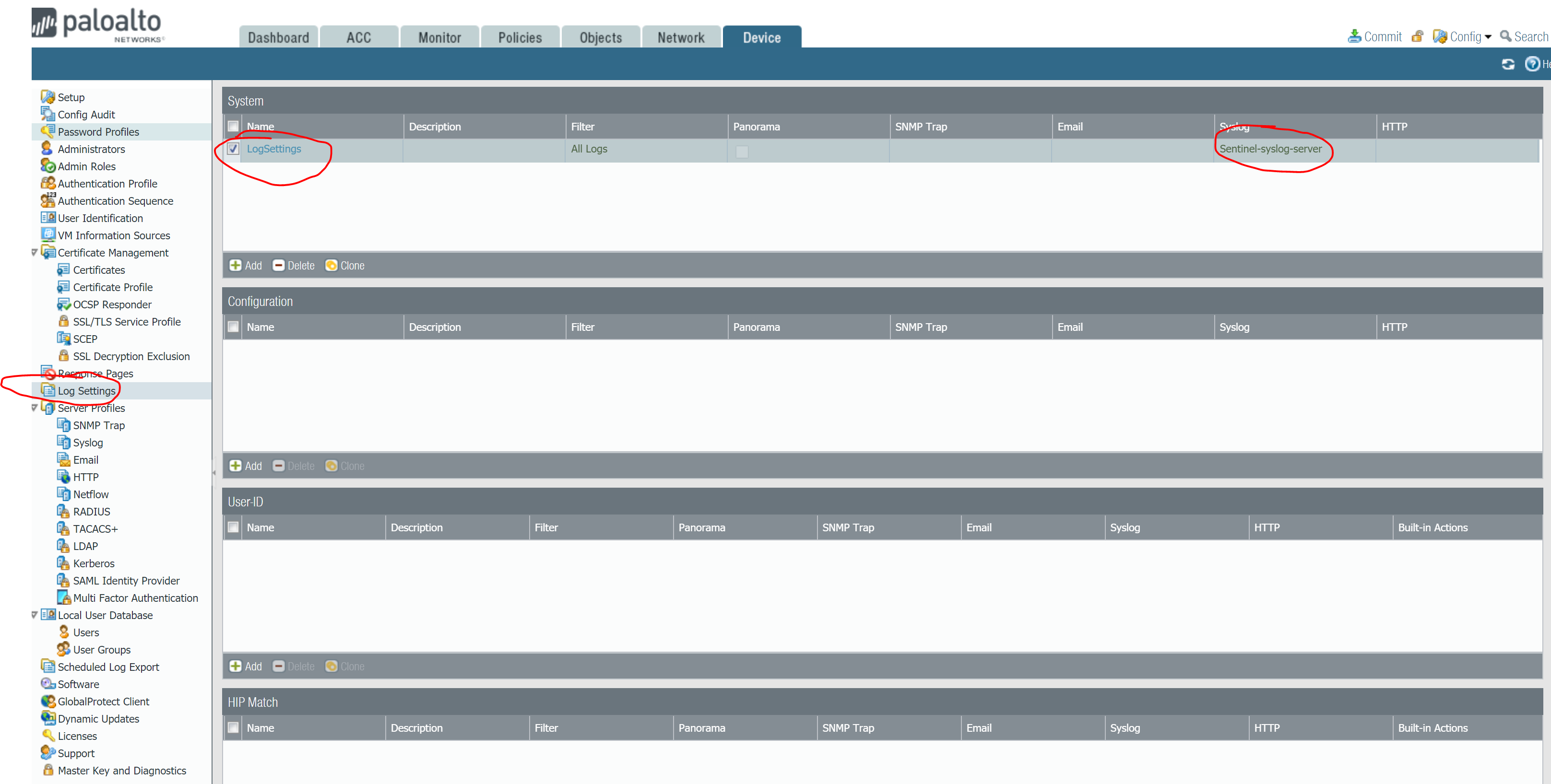
I have also enabled Log Settings to filter All Logs and send to the syslog server that was just created
Finally on the Palo Alto console, you will need to use the Log Forwarding profile with your Policies. In my case I will log at session-end for allow_http traffic and session start & end for deny_all policy
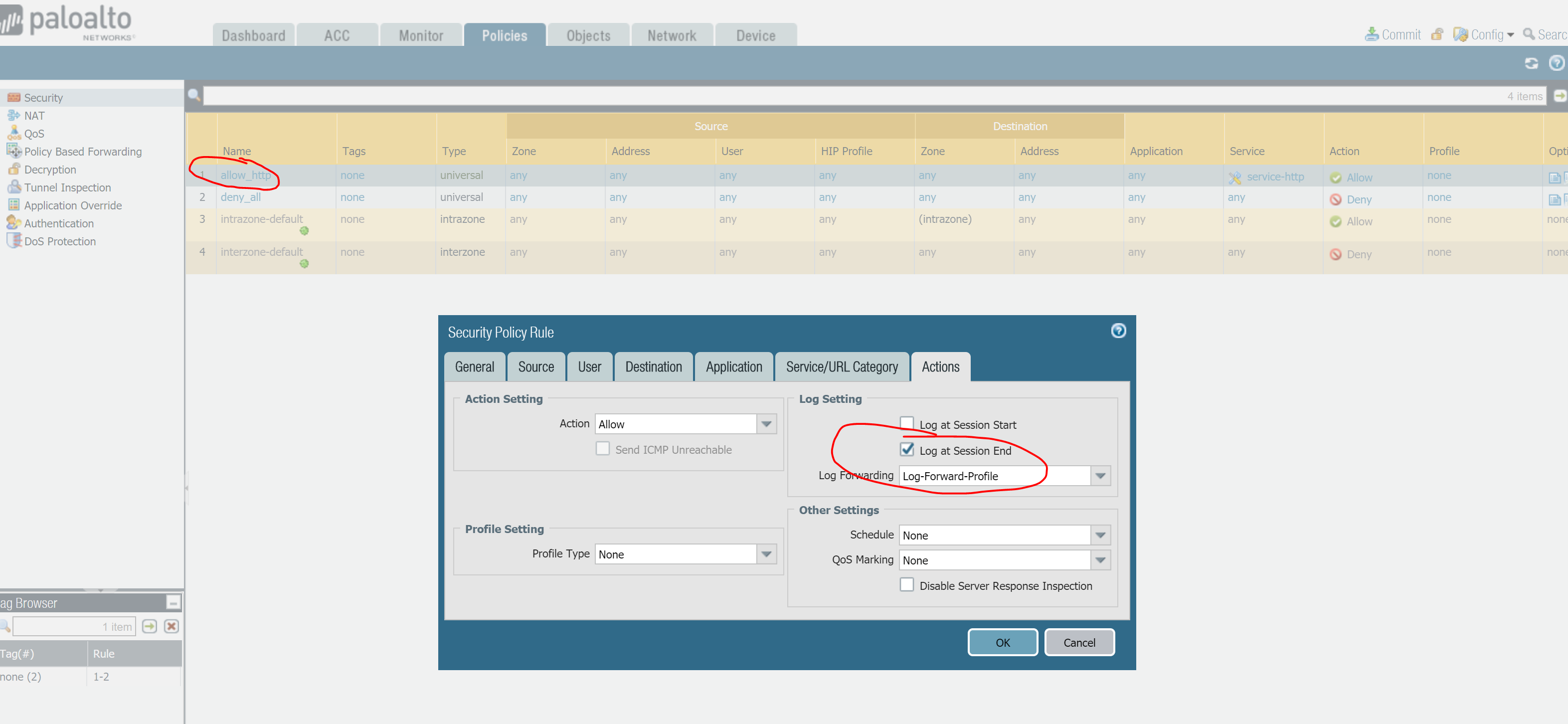
Don’t forget to commit changes in Palo Alto to make them effective!
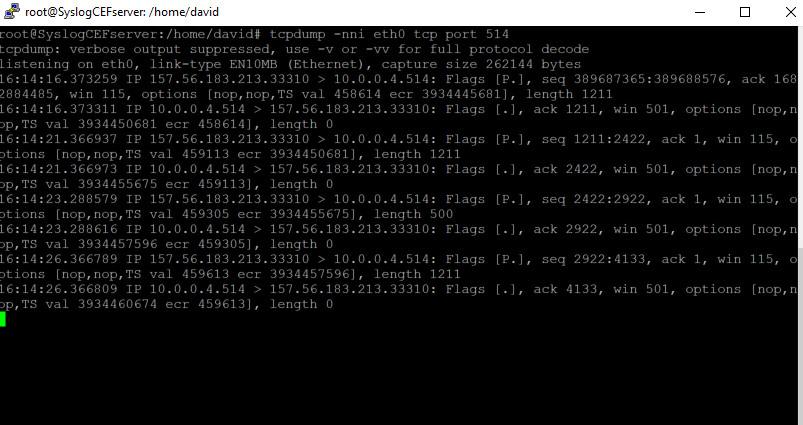
On the Azure side, I will start checking that my syslog collector is receiving those logs, so a simple tcpdump on port tcp 514 will do the job
At this point you should see your Palo Connector on the Sentinel console turning ‘green’ which means the syslog collector is doing its job by storing the syslog logs with the right format into the Log Analytics workspace
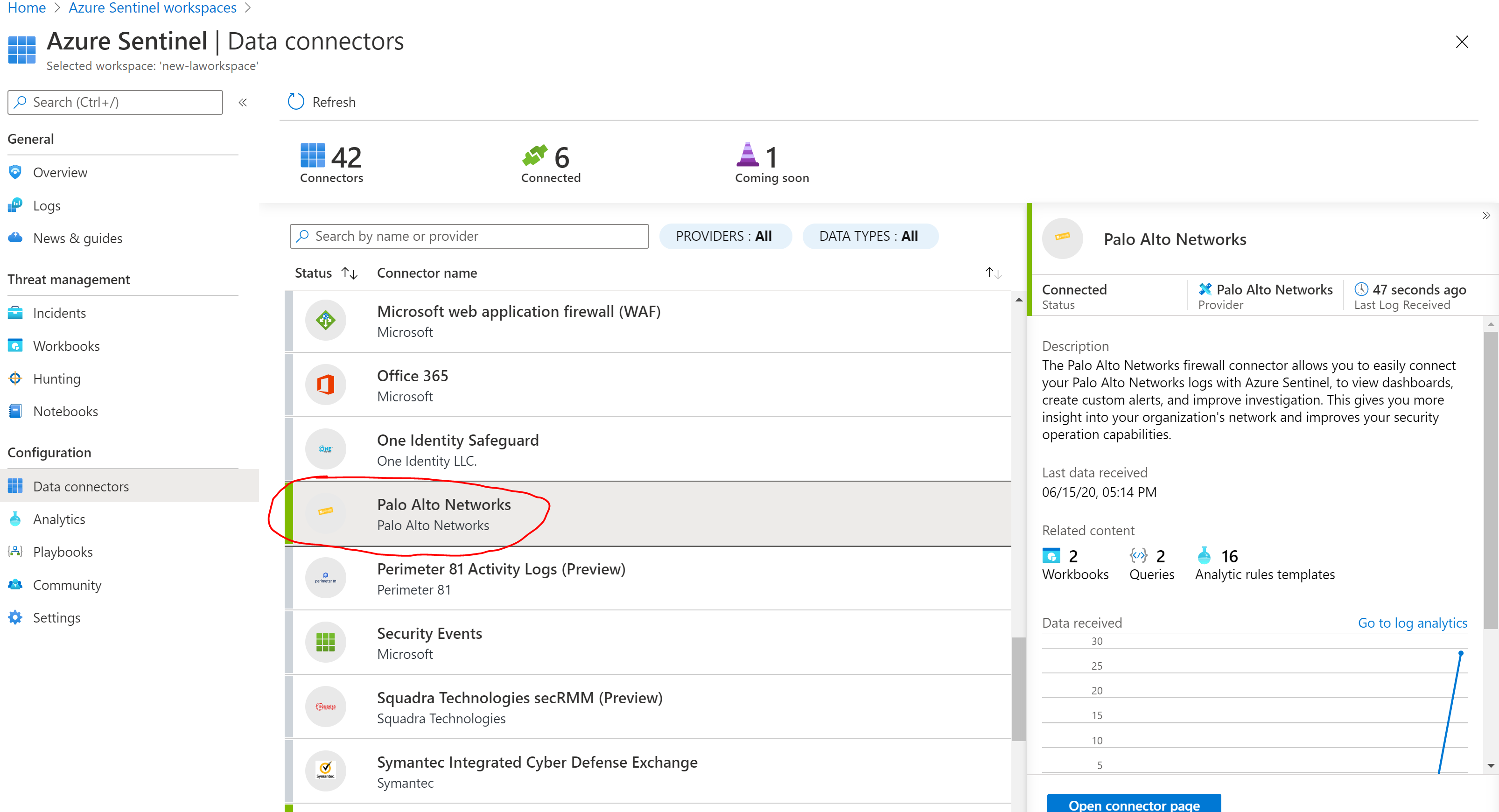
Palo Alto logs will be stored on the CommonSecurityLog table of Log Analytics, so that’s how you start searching for your logs
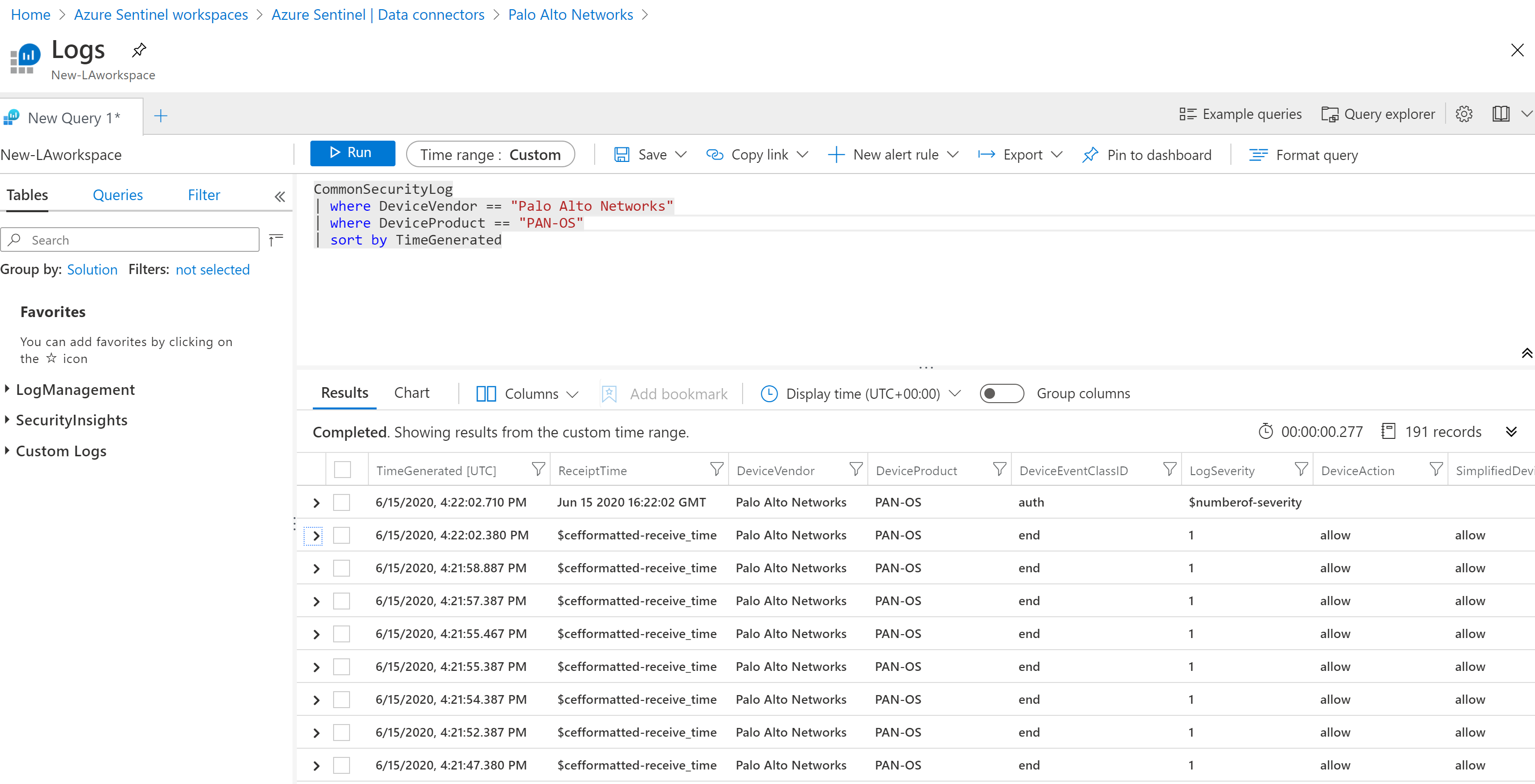
Finally, don’t forget to enable the relevant analytic queries for these logs
0 Comments